Posted 01/08/2025
One of the most complex challenges during mergers, acquisitions, or divestitures is establishing secure connectivity between corporate IT environments. Even with tight technical restrictions and strict security protocols in place, there’s often immediate pressure to enable user collaboration and access to shared resources.
That’s where rapid identity synchronisation between organisations becomes critical – it enables user accounts to function across both environments, laying the groundwork for productivity from day one. However, differing security postures and risk tolerances between organisations can introduce additional layers of complexity that must be navigated carefully.
IT security teams often (and rightly) take a hardline stance on the introduction of new services and will not be willing to open access and connectivity until complete due diligence of the end-to-end solution had been undertaken. This could take a significant amount of time and effort.
In many cases, organisations will simply not take the risk of exposing any of their internal servers – especially their Active Directory Domain Controllers externally, under any circumstances.
When connectivity is allowed, it’s normally limited and tightly controlled. For example:
Another common challenge is that there are IP subnet conflicts preventing convergence. Changing IP ranges to large waves of infrastructure is a lengthy, complicated process. It’s not uncommon for organisations to have the same internal IP ranges, such as 10.x.x.x and 192.168.x.x.
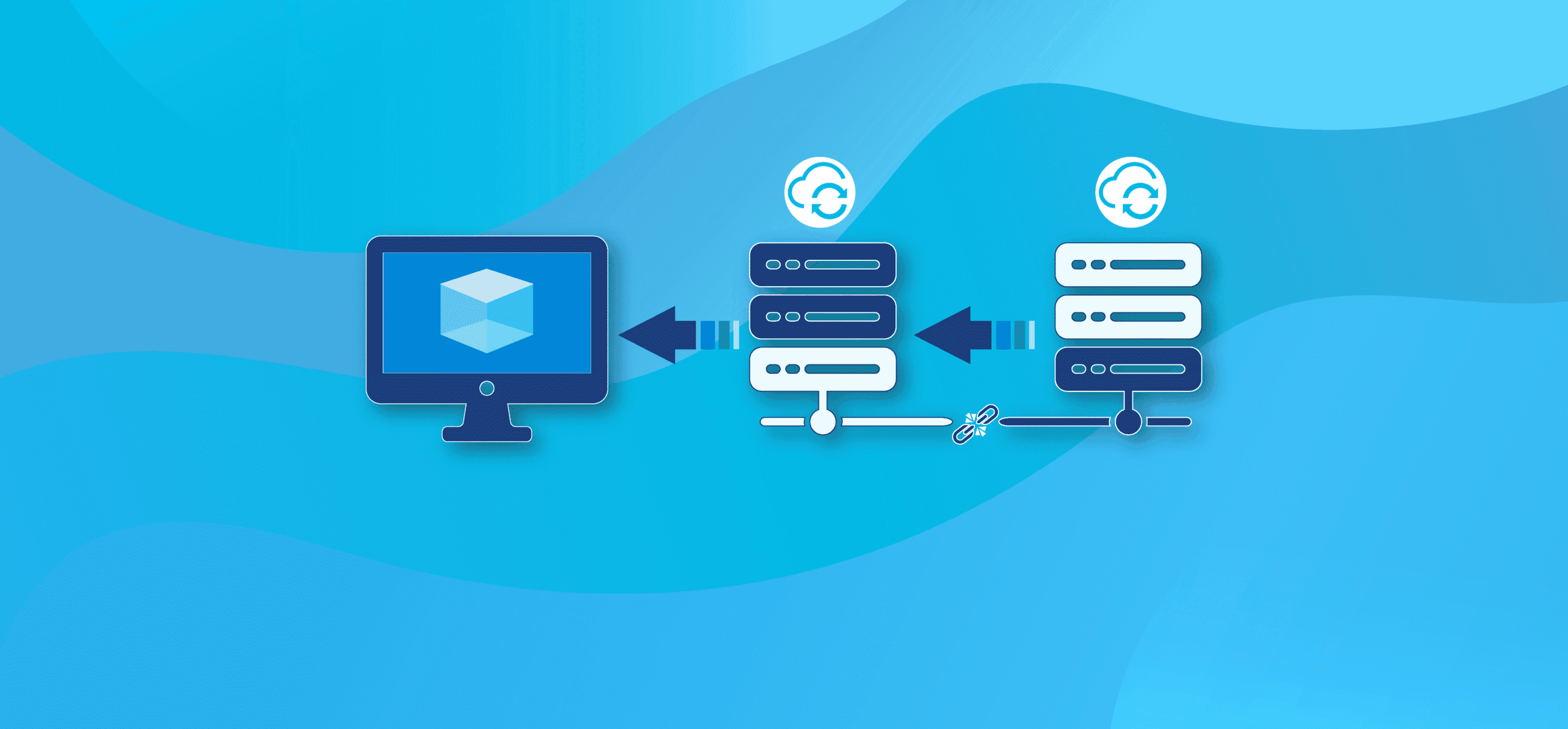
A scenario we often encounter is when a partner hosts PowerSyncPro services for their client and needs to establish connectivity for PowerSyncPro Directory Synchronisation or Migration Agent to their customer’s Active Directory without exposing anything over the GWAN.
We also see long-term coexistence scenarios, where both organisations remain connected for an extended period. In such cases, connectivity is typically restricted to the bare minimum services needed to function securely and efficiently.
In consolidation initiatives, key stakeholders and C-level executives want to see tangible progress early. There’s strong pressure to enable collaboration quickly, even when full network integration or IT unification is still underway.
Often, the initial goal is perception and productivity: presenting a unified corporate identity. This could include:
PowerSyncPro accelerates these early outcomes by enabling rapid, secure identity synchronisation – even in high-security disconnected environments. A common first step is establishing a greenfield Active Directory resource forest that acts as a central trust hub. From there, users and groups can be synchronised bidirectionally, laying the groundwork for comprehensive consolidation.
With early identity integration in place, organisations can begin decommissioning duplicate infrastructure, aligning networks, and planning for tenant-to-tenant migrations – all with measurable progress in the first 30 days.
PowerSyncPro was designed by experienced network & Active Directory architects who have faced these challenges out in the field. They understand what features need to be available to facilitate companies embarking on identity consolidation, synchronisation or device migration under challenging network designs and restrictions.
There are four main components that can be integrated in various configurations depending on the environment:
As the orchestration server, this is where your directories (Active Directory, Entra ID, Google) are configured, and where profiles are created to determine object matching, synchronisation logic, and the scope and configuration of what you want to achieve. PowerSyncPro uses a metaverse concept (import all, sync, export) and relies on SQL for its database.
PowerSyncPro has enterprise-grade synchronisation capabilities for your scoped objects and attributes and can manipulate them with advanced re-write rules – using graphical “IF, THEN, ELSE” formulas known as complex expressions.
You can communicate via LDAP directly with Active Directory if you have uninterrupted network line of sight, or leverage some of the other components: Proxy Agent, Remote Sync Agent and Password Agent.
This agent (which commits or reads changes) can be placed on any member server and become the endpoint for the directory synchronisation for the Active Directory domain controllers it has line of sight to. If required, the Remote Sync Agent can communicate over the internet with appropriate firewall rules in place back to the PowerSyncPro server.
No inbound ports need to be open on the Remote Sync Agent server. A single configuration is used to communicate with the PowerSyncPro server endpoint address. The Remote Sync Agent will communicate using gRPC (HTTP/2 based) and REST standards back to PowerSyncPro server. Alternatively, you may wish to configure SCP records, and it will go via the Proxy Agent (if also deployed).
One of the features I love best is that the credentials for the environments are stored on the Remote Agent server and not the PowerSyncPro server, making a clear demarcation line of security without needing to share credentials with a 3rd party.
In high-security environments, organisations may have disabled RC4-based password hashing (NT hash) within Active Directory due to its deprecated and insecure cryptographic profile. As a result, traditional hash-based password synchronisation is no longer possible.
The PowerSyncPro Password Agent addresses this by using a lightweight password filter installed on each domain controller capable of processing password changes. This filter securely captures password changes at the time of entry and transmits them using end-to-end encryption to the target environment.
Password data can also be securely streamed via the PowerSyncPro Proxy Agent, allowing this solution to function even in restricted or segmented network environments without opening additional inbound firewall ports.
If your policy prohibits Remote Sync Agents or Password Agents to perform outbound internet connections, there are several industry gold standard methodologies that you can implement using PowerSyncPro features to increase security and reliability.
The Proxy Agent can act as the endpoint within your infrastructure or a DMZ to send or receive updates for object attributes, SID History and password changes then relay (stream) them over the network (or internet) to the PowerSyncPro server for onward processing.
Proxy Agent is a lightweight configuration and only acts to transport the communication, so no credentials are stored.
To initiate secure registration with the PowerSyncPro Server, each Sync and Password Agent must be installed and configured using a one-time-use Pre-Shared Key (PSK), generated by the administrator. During installation, the agent also receives a private certificate, which is used to encrypt all future communication with the server using its corresponding public certificate.
Once installed, agents appear in the PowerSyncPro console in a pending state. To become active, they must be explicitly approved by an administrator, ensuring that only trusted hosts are integrated into directory profiles.
Further securing the communication path, all traffic between agents and the PowerSyncPro Server is transmitted over HTTPS using gRPC, with mutual TLS (mTLS) enforced via public/private certificate pairs on each endpoint. This layered approach ensures strong authentication, confidentiality, and integrity at every stage of communication.
What follows are some example configurations which you could design and deploy.
PowerSyncPro hosted in a different organisation infrastructure, where identity synchronisation must occur through a multi-hop process. In this scenario, only machines located within a DMZ are allowed to access the internet.

RC4 disabled in a high security environment where you need to synchronise passwords.

Migrating devices and/or synchronisation of identities when the PowerSyncPro server does not have line of sight to a domain controller:

High availability and redundancy of remote and proxy agents to synchronise identity:

We’ve helped organisations around the world simplify even the most locked-down environments. Get in touch today and let us show you how we enable secure, compliant directory synchronisation – even with no direct connectivity.